Visao
See what's happening in your application. Find defects, analyze architecture and do what's right for your project.
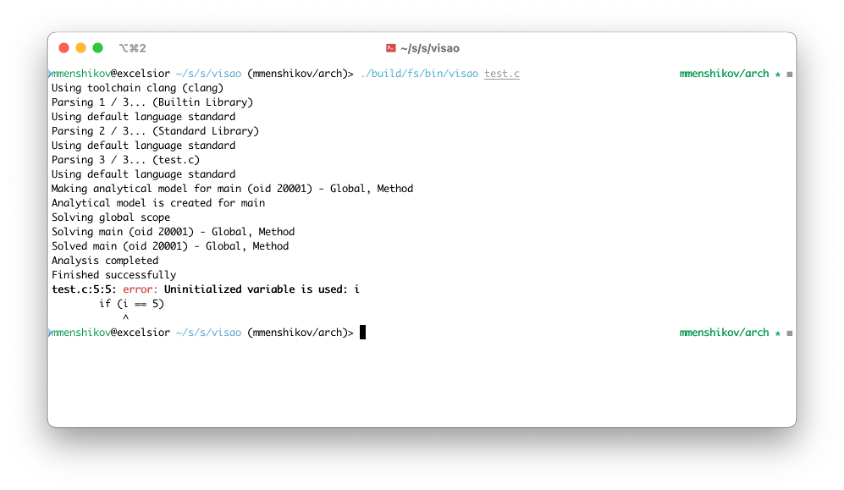
Future-proof solution
- Trace underlying issues, not known patterns.
- By knowing code of libraries, our detectors work not on patterns, but on issues that these patterns lead to.
- Solid mathematical foundation.
- Abstract Interpretation, Model Checking, Satisfiability Modulo Theories - everything that can increase precision.
- ... and a lot of hacker specifics.
- The mathematical models are bound to high-accuracy low-level machine descriptions.
Proactive protection
- Find architectural issues.
- Software design problems are the primary source of future vulnerabilities. Identify them with ease.
- Investigate issues on the edge between modules.
- Spot the issues on interconnection between your project and third-party libraries.
- Recognize implicit contracts.
- Trace the difference between expectations and reality in the code.
TS Factory
Test your device or an interconnected project with industrial strength. Project website
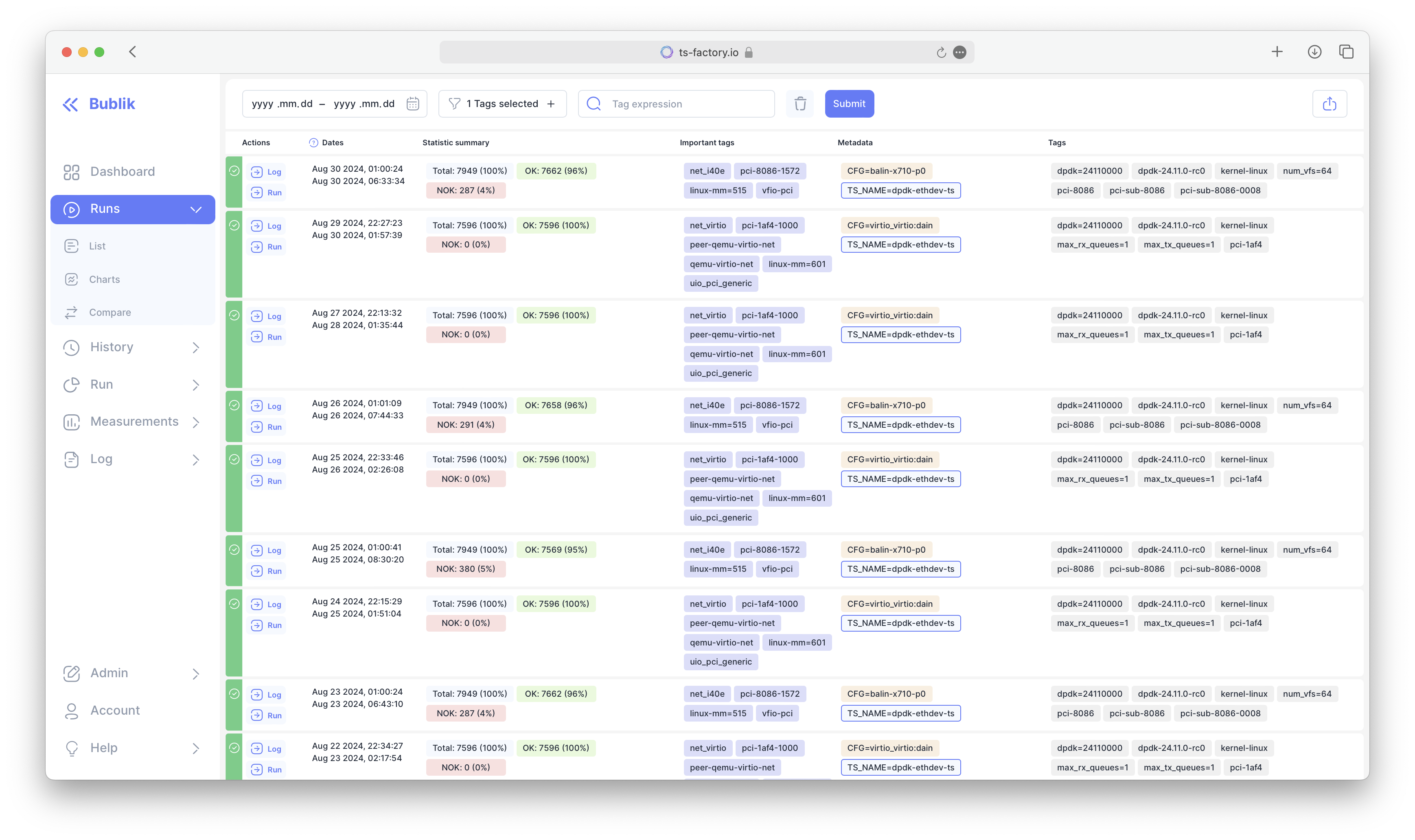
Industrial strength
- Time-proven.
- Large companies have been successfully using TS Factory for more than decade. Under huge loads with years of logs.
- Versatile.
- Modules for many use cases: from serial console manipulation to high performance traffic generation.
- Truly multi-agent.
- Hundreds of cooperating agents, all driven from the easy-to-write tests.
Delta
Run lightweight sensor anywhere. Get insights on how your application runs. Detect security breaches. Collect logs - and pass it on for analysis.
What you need wherever you need
- Monitor your application.
- Take logs, CPU load data, API/system call usage. All with the lowest possible memory and CPU footprint.
- No more hacks.
- Fingerprint the device. Detect breaches and disconnect the broken device from the network.
- Keep track of your deployments.
- Report deployments to the analysis server and know your ecosystem.
Evolucao
Collect the data from Visao and Delta. Visualize it. Get actionable insights.
Massive data at your fingertips
- Explore the project.
- Include all source files and view them as a part of a bigger project.
- Verify dependencies.
- Don't forget about libraries that you use. They are no less, or even more important for security.
- Visualize the complete lifecycle.
- From writing the first line of code to deployment — everything covered.
Ready to see demo?
Drop a line to us and we'll see what we can do for you.
Fill in the form
Give us 1-2 business days to respond, or, contact us by E-Mail directly.