Secure code starts at compile time
Create, analyze, test and deliver your software with our tools.
Products
We develop a universe of products to perform analysis of software - and beyond.
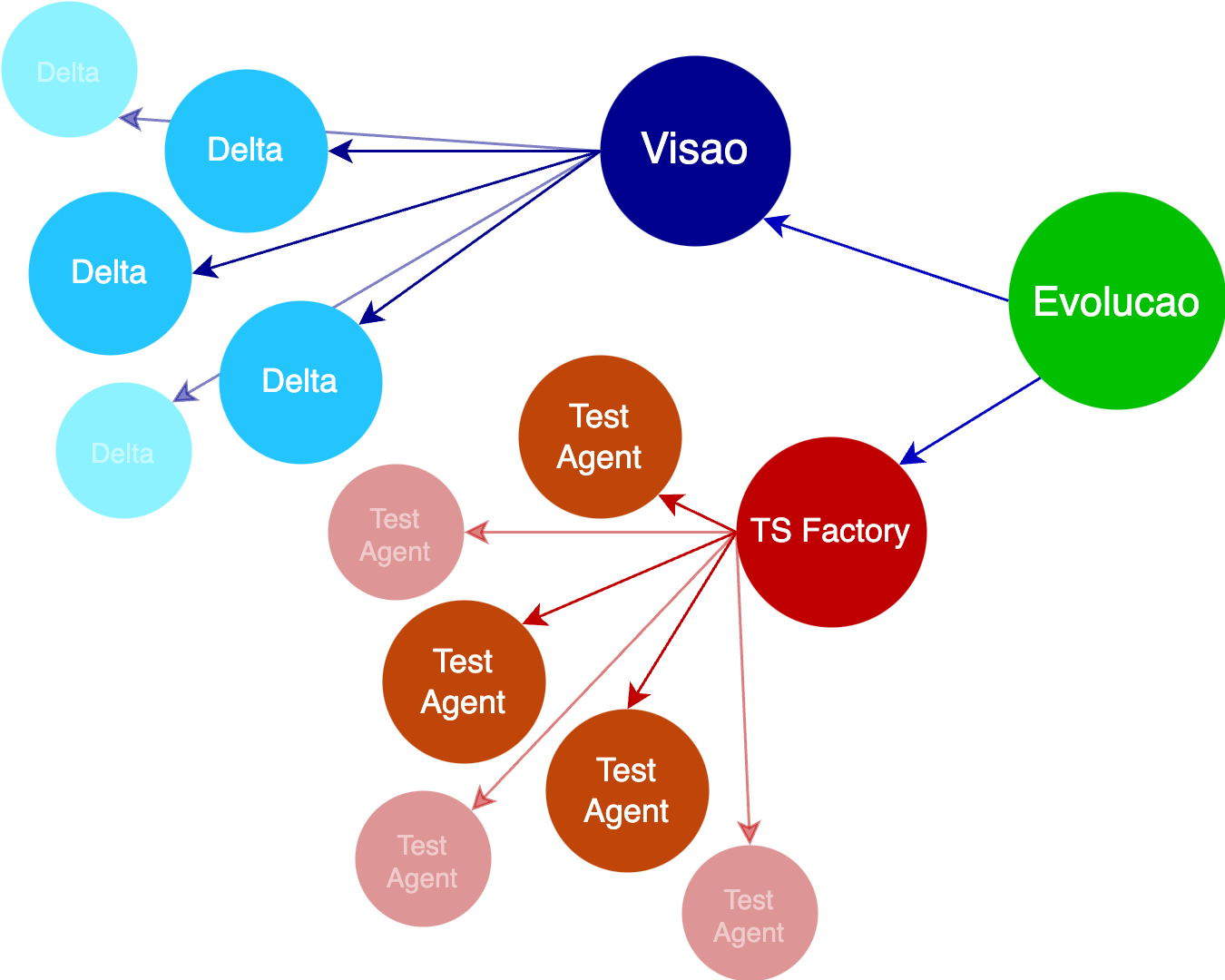
Cover all the vectors
Defects might come from all sides. Take proactive approach and close vulnerabilities before the are found by the user.
- Analyze the code using Visao.
- Many languages, single analyzer. Mathematically sound and easy to integrate.
- Test the project using multi-agent TS Factory.
- Simulate high load. Run testing commands from many hosts simultaneously. Reconfigure hosts in runtime.
- Monitor the deployment using Delta.
- See how your app behaves. Detect security breaches.
- See the overview using Evolucao.
- In one place.
Take control of your app
Your software is a lot more than just the code.
It is also an idea, and all the dependencies.
See how they all fit together.
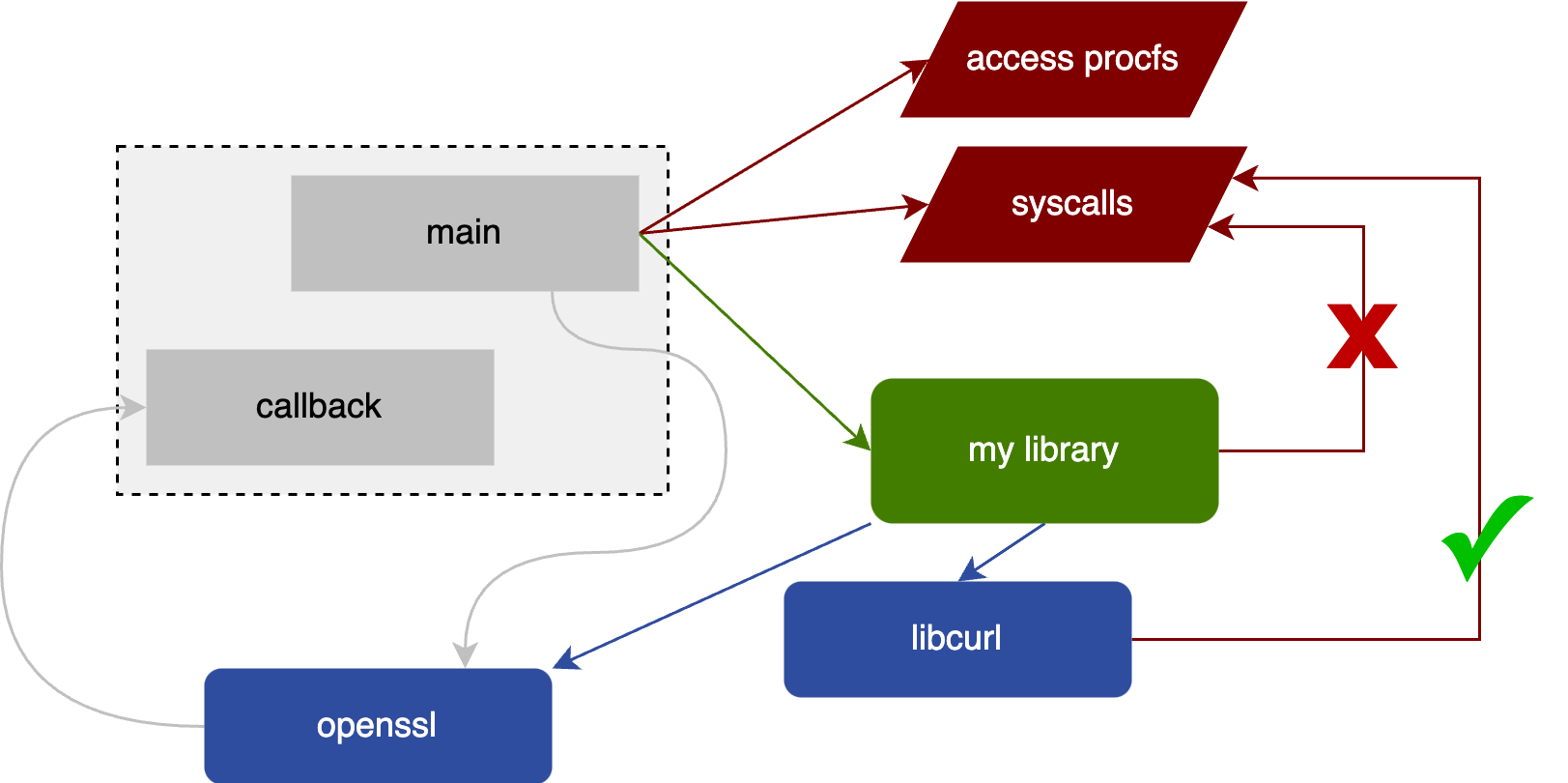
Services
Make no mistake with our help. We can architect, code and secure your software with industrial strength.
Secure engineering
Building secure software is hard. We are aware of the state-of-art techniques to do that and are ready to lend a hand to you.
Development tools
We believe that building secure software is only possible if you control the stack. Complex technology stacks are our cup of tea.
- Analyzers and linters
- Compilers
- Debuggers (+reversible)
- IDEs
- Code generators
- Build systems
Electronics/Networking
We were making many electronic devices. Many of them were successfully launched in the wild.
- Routers and extenders.
- Smart watches.
- Wi-Fi, including Mesh.
- High-performance networking.
- System-on-Chip integration, custom Board Support Packages.
Security audit
Not sure about the security of your software? Our experts may check it for you.
- Defects
- Architecture and composition issues
- Security risks
Ethical reverse engineering
Lost sources? End-of-life driver? We may either help you understand what was going on there, or even rewrite it.
- Any architecture (x86_64, ARM, MIPS, ...)
- Any detalization level
Infrastructure
Is your infrastructure ready for building high-quality software? Setting up Continuous Integration is our daily job.
- Setting up dedicated and cloud servers.
- Any continuous integration solutions.
- Virtual Private Networks (VPN).
Plans
Affordable to any type of business.
Most popular
Basic
Contact usPerfect fit for most projects
- Extended + custom sensors
- Extended integrity checks
- Product support
Enterprise
Contact usComplete overview of your software projects
- Checks tailored to your projects
- Custom views
About us
We are professionals from various fields passionate about making impactful analysis tools.
(hover to see more information)
Contact us
Tell us what you think
What to ask?
- Get a copy of software (licensing questions)
- Questions about the software
- Request a quote for services
Fill in the form
Give us 1-2 business days to respond, or, contact us by E-Mail directly.


